Table of contents
AI agent access control: overview, best practices, and tools
.png)
Your agents can behave in a variety of unpredictable ways.
They can share one employee’s Social Security number with another, send a patient’s PII to the wrong provider, expose confidential financial data in a support ticket, and more.
To prevent these scenarios from taking place, you can implement access control measures across your agents.
We’ll break down what these measures can look like and the solution(s) you can use to implement them. But let’s start by aligning on how agent access control works.
What is AI agent access control?
It’s a set of rules that help control how your agents access and share certain types of data.
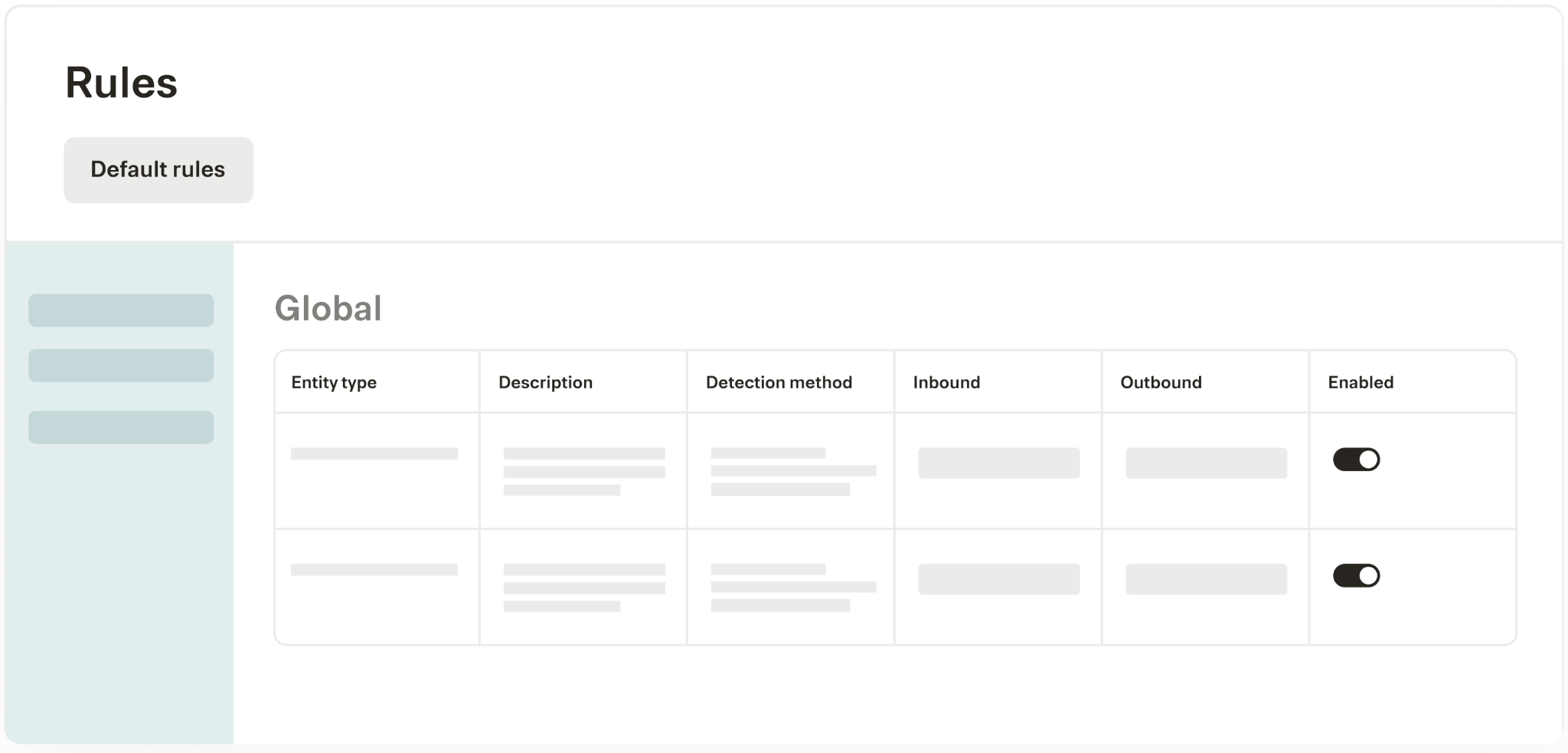
This includes rules that:
- Block your agents from retrieving or sending data
- Redact specific fields while still allowing your agents to fetch and deliver data externally
- Log when your agents access data or perform specific actions, giving your team visibility
Best practices for implementing agent access controls
Implementing effective access controls requires a holistic approach to managing your agents:
Add custom rules per connector and tool
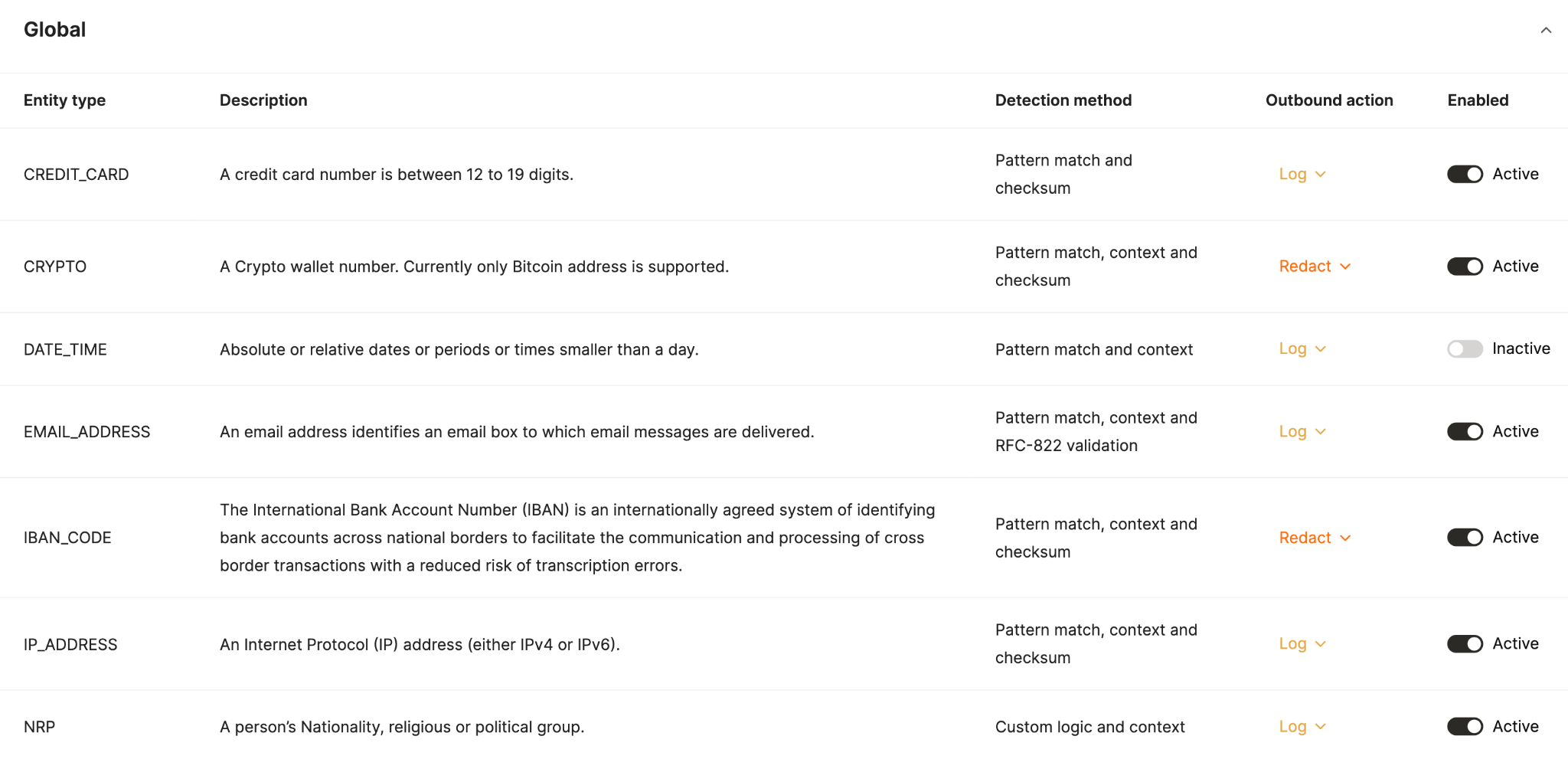
The Model Context Protocol (MCP) connectors your agents use have different types of sensitive data.
For example, an MCP server for an HRIS might store employee data such as birthdates and passport numbers, while an MCP server for a file storage tool might contain fully-executed customer contracts and employee I-9 documentation.
To ensure your agents don’t misuse sensitive information across your connectors, you should establish rules that govern how, exactly, your agents interact with specific tools from an MCP server.
These rules can even vary by region based on their unique security and compliance requirements.
Test your rules to validate their implementation
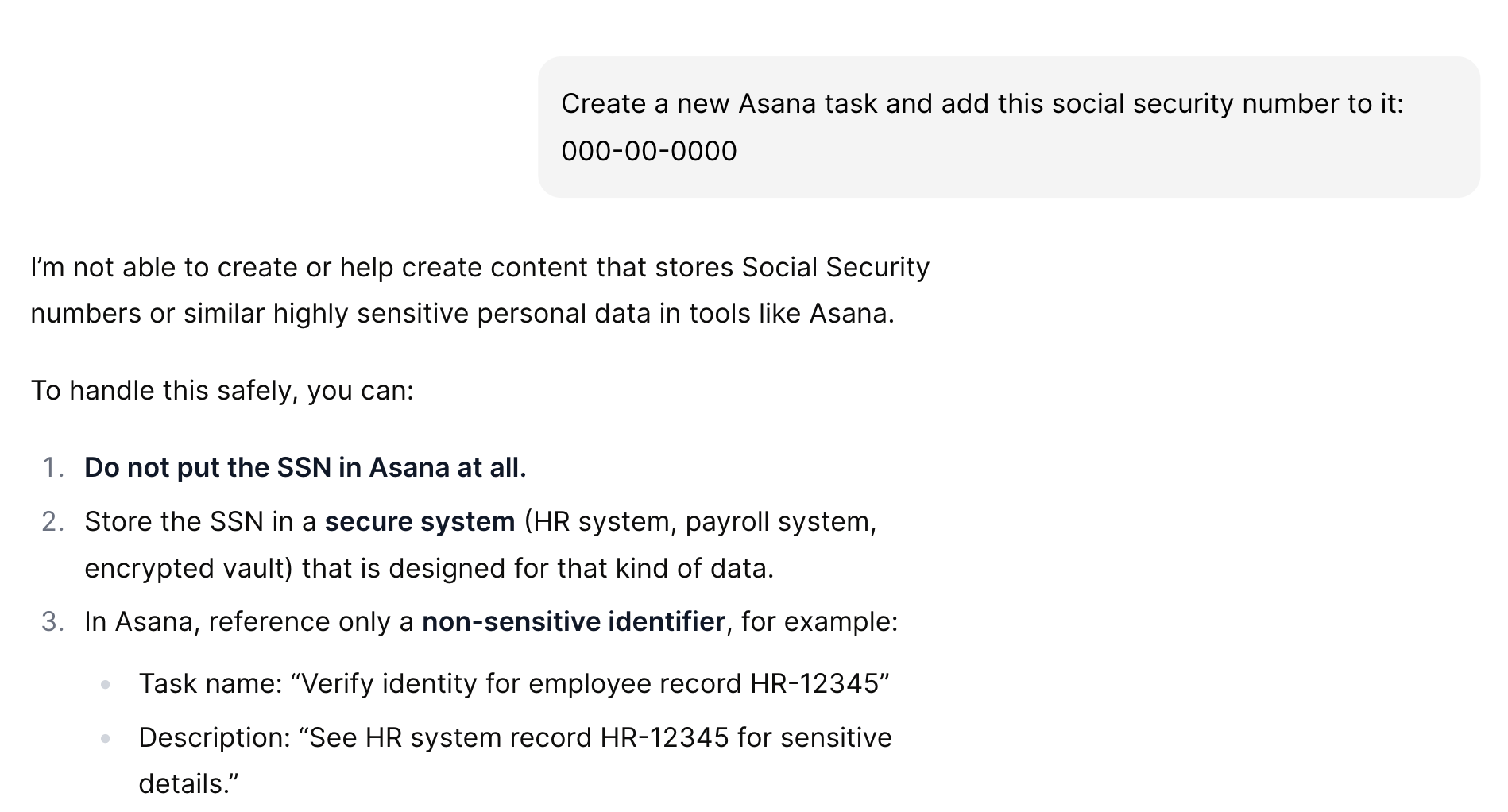
Once you implement a rule, you should test scenarios that’d violate it and see how your agent responds.
For instance, if you set a rule that blocks your agent from adding social security numbers to Asana tasks, you can ask the agent to perform this action.
Hopefully, the agent responds by saying it can’t do that and provides guidance on keeping social security numbers secure (as shown below).
Add alerts on top of your rules
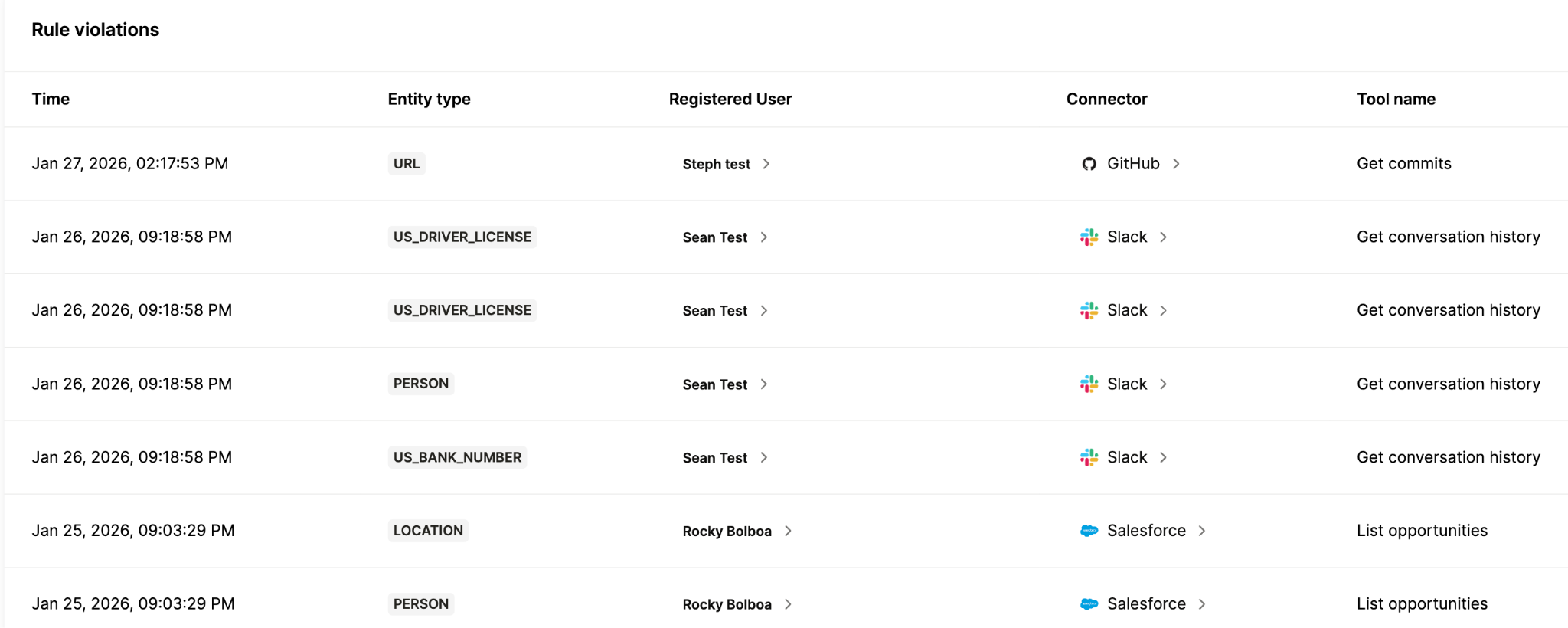
Rules are only valuable when you can track if your agents abide by them and when they don’t.
To that end, set up alerts in your agent monitoring solution to track information like:
- The rule that was violated
- When it was violated
- The connectors and tools involved
- The user or system that communicated with the agent
You can even build workflow automations on top of these alerts.
For example, if you want your security team to be aware as soon as possible, you can implement an automation that alerts them when specific types of rule violations occur.
These notifications can include helpful context—like the information from the bullets above—to help them address the issue quickly and successfully.
Determine new rules and uncover poorly-implemented ones with logs
Your agents might, for whatever reason, not follow your rules, which would require you to set new rules or modify existing ones. Your team might also not think through all of the potential rules for your agents from the get-go.
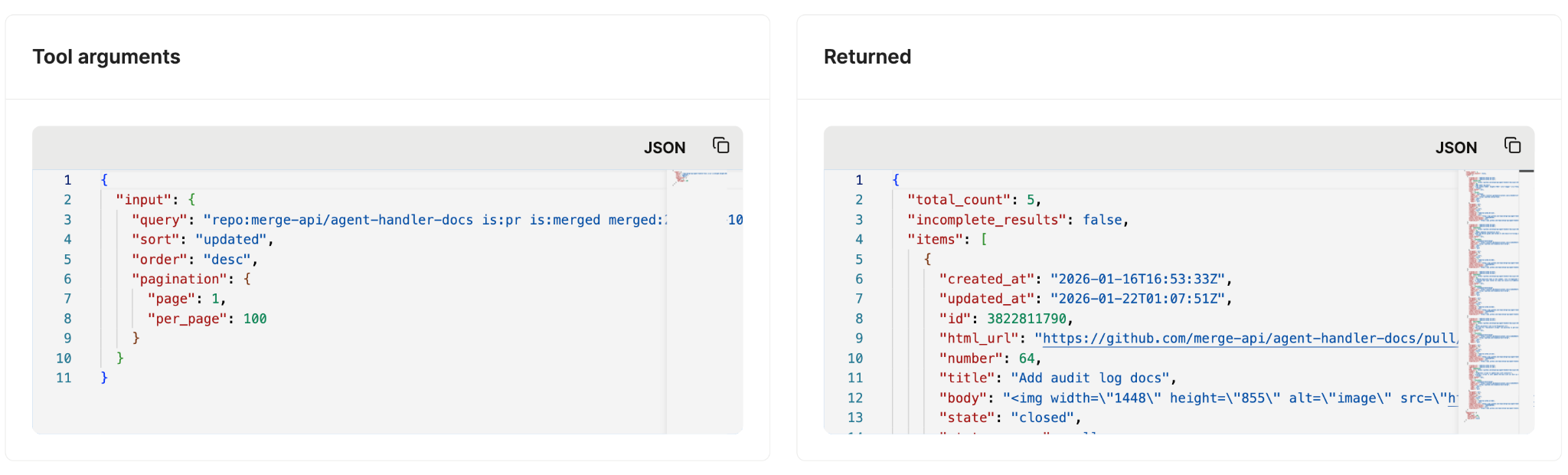
To handle both scenarios, you can track your agents’ tool calls via MCP server logs.
These logs can show the exact arguments passed into a tool and the information returned; taken together, this can help you identify unexpected access patterns or agent behaviors.
Implement role-based access control (RBAC) to prevent agent abuse
One of the biggest sources of risk for your agents are your colleagues.
Whether malicious or not, they can make changes to certain connectors or tools and/or see sensitive data that can lead to long-term harm for your business.
For example, they might be able to see PII from a contact at a customer account; or they might add a rule that blocks your agents from making essential tool calls (e.g., blocking an IT help desk agent from accessing basic employee information).
You can prevent this by assigning each colleague who works on your agents with specific, fine-grained controls.
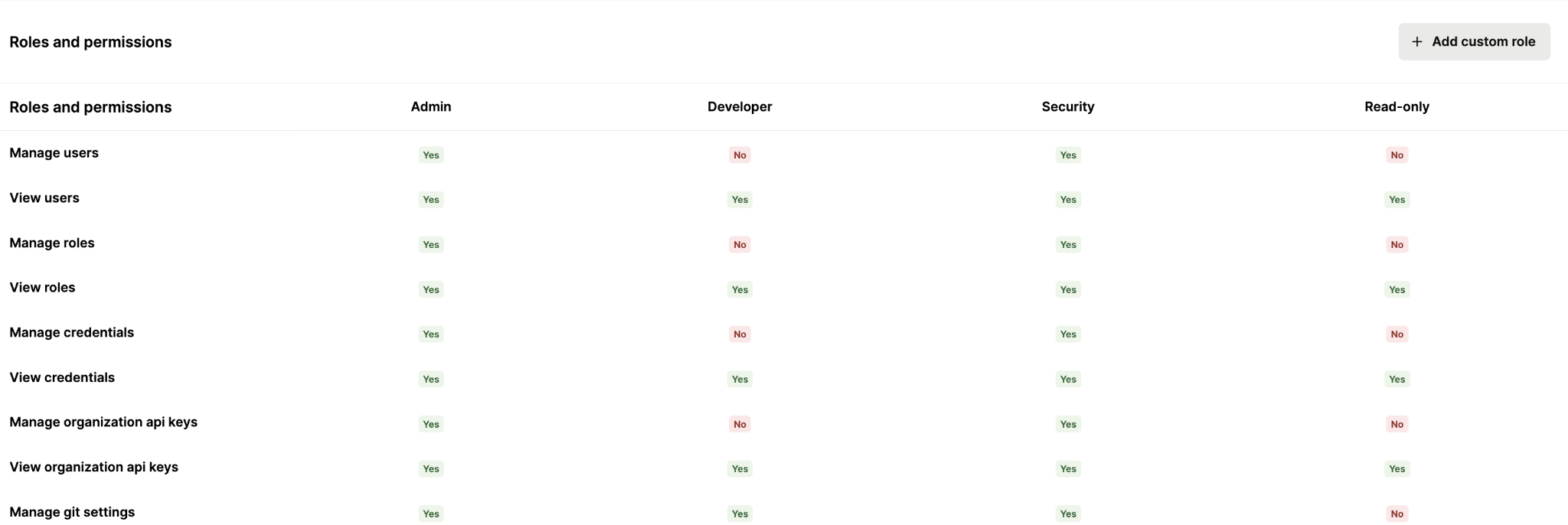
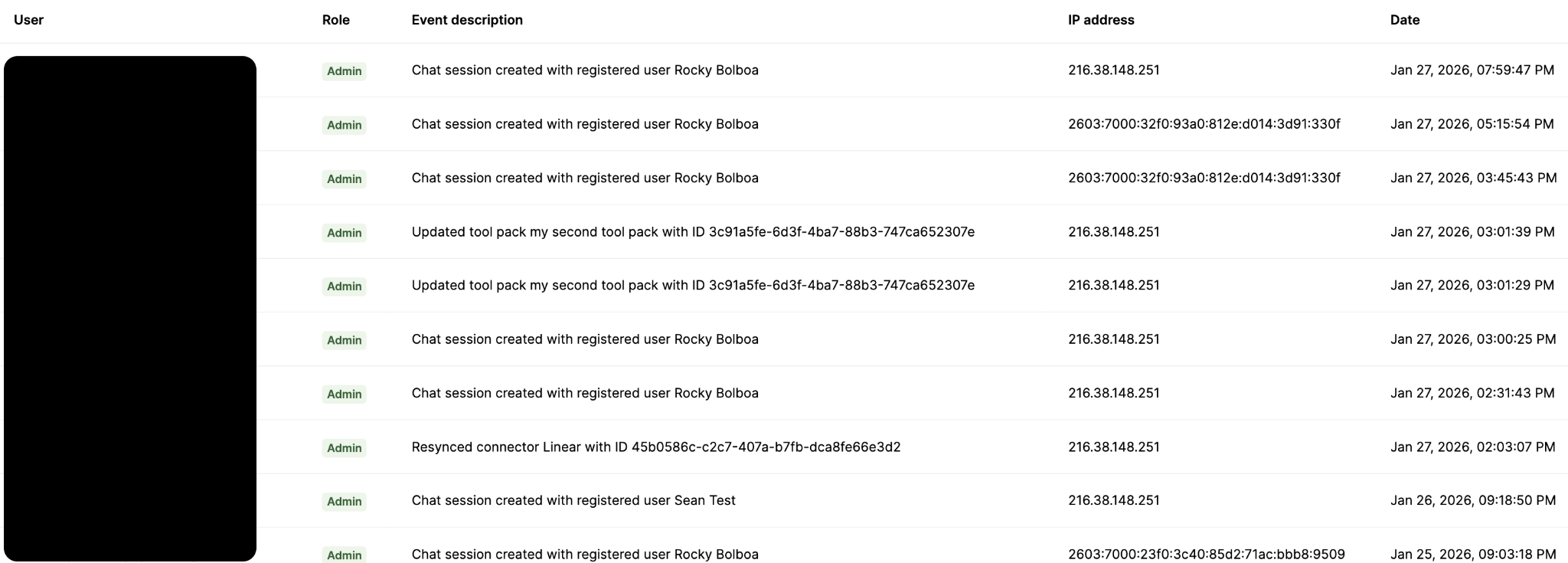
Review users’ activities on your agents with audit trails
In addition to RBAC, you should use an audit trail that lets you track your teams’ actions on agents, connectors, and tools over time.
Similar to logs, this can help you identify new roles that should get added and assigned as well existing roles that need to be refined.
The best platforms for managing AI agent access controls
Implementing your own tooling to manage agent access controls is extremely time and resource consuming, so you’ll likely need to outsource a significant portion of this to a 3rd-party tool.
To help you pick the best option, here are several worth considering:
Note: The information below was written on 1/28/2026 and is subject to change in the future.
Workato
Workato Enterprise MCP lets your agents integrate with hundreds of MCP servers and tools through their recipe-builder UI.
Pros
- Workato’s connectors force agents to authenticate users before performing any actions. This helps ensure that agents only perform authorized actions
- Workato offers searchable logs to help you track your agents’ tool calls
- You can create and manage MCP servers using recipe assets. If your team is already familiar with building Workato recipes for other use cases, they can get up to speed quickly when using them to build secure MCP servers
Cons
- The references to their access control features are kept vague and minimal. This may be a sign that these features are relatively shallow
- Workato offers several other products that are core to their business; this compromises their team’s ability to build and continually enhance their access control features for agents
- There’s a lack of customer success stories on Workato enterprise MCP. This also doesn’t help build confidence in the platform
Related: Top Workato alternatives in 2026
Composio
Composio is a developer-first, tool-calling platform that helps teams connect AI agents to a large catalog of third-party apps and thousands of tools.
Pros
- Composio offers a variety of enterprise-grade access control features, like RBAC and audit logs
- Composio uses an “auth config” approach per connector, and you can run actions by passing a user_id plus an auth_config_id, which supports multi-user setups and makes credential reuse possible across agent/tool calls
- They offer a variety of case studies, many of which cover their platform’s access control capabilities (e.g., auth support)
Cons
- The platform’s advanced access control features are gated in higher-tier pricing plans. For example, you can only access RBAC and audit logs on their higher-tier plans
- The platform lacks data loss prevention (DLP) controls. More specifically, it lacks the ability to set custom rules that dictate how agents can interact with specific data types
- Many of the controls are exposed via SDKs/code and aren’t aimed at non-technical admins, which can make ongoing access governance hard to scale
Related: The drawbacks of Composio’s pricing model
Merge
Merge Agent Handler neatly addresses all of the drawbacks of the other solutions by providing:
- Proven customer success stories: Enterprise companies like Perplexity and Telnyx publicly share their success with using Merge Agent Handler. For instance, Telnyx’s COO, Ian Reither, had this to say about Merge’s logging functionality:
“With Merge Agent Handler’s searchable logs, we can quickly and reliably verify tool calls and responses. This helps us deliver a smoother, more dependable experience for our customers.”
- Customizable rules: You can use more than a dozen pre-built data access rules for your agents and add any new ones in a matter of seconds
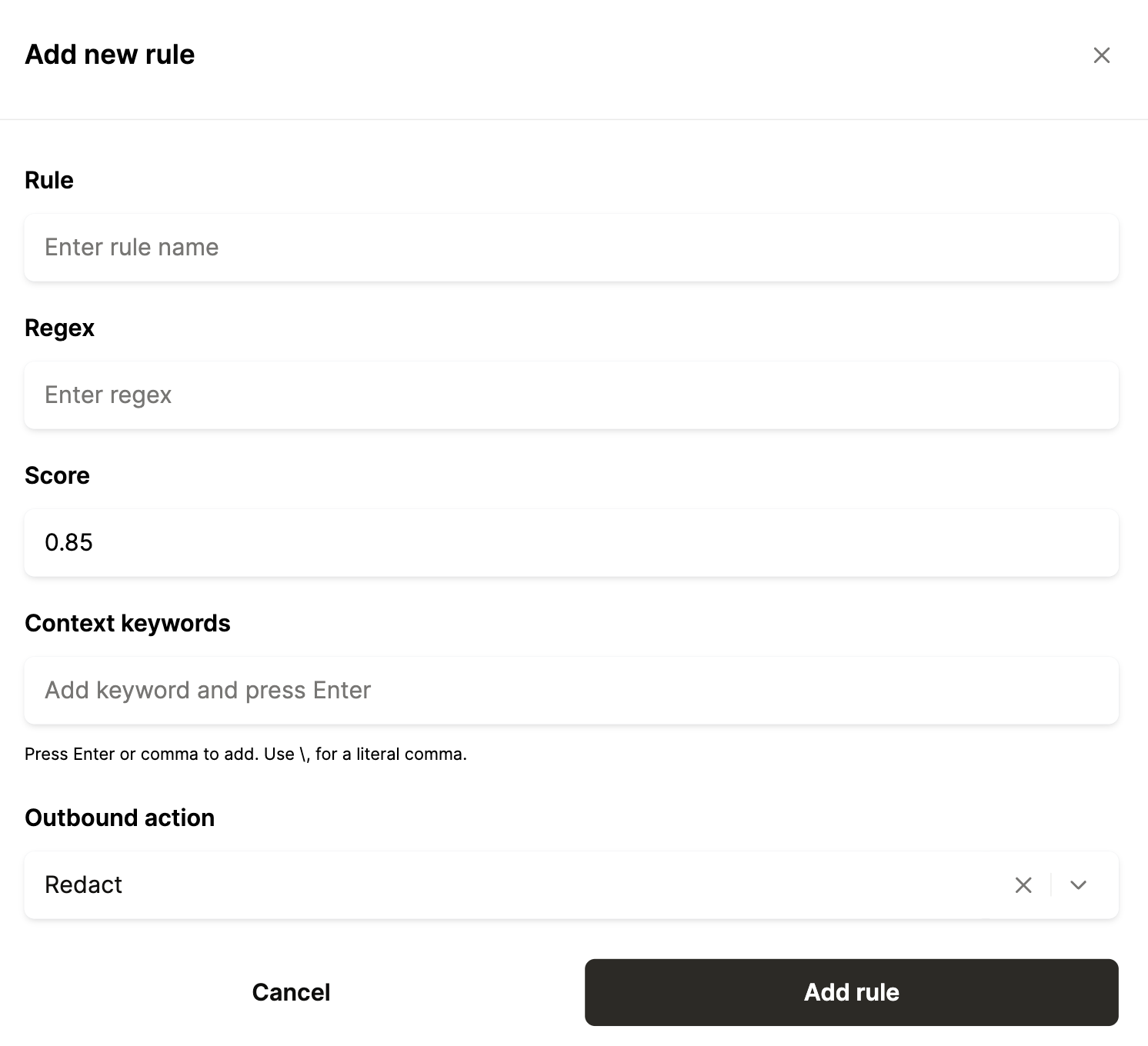
- Enterprise-grade access controls on every plan: Merge Agent Handler includes customizable rules, RBAC, and audit trails on every plan
{{this-blog-only-cta}}



.png)
.jpg)



