Table of contents
The 3 best AI agent authentication tools in 2026
.jpg)
As you help users connect your AI agents to MCP servers, you’ll need to implement authentication flows that prevent unauthorized access and protect sensitive information.
Developing and maintaining these authentication flows yourself likely isn’t sustainable; it means investing time and resources into security infrastructure that distracts from your core product work.
To that end, we’ll walk you through several tools that allow your users to authenticate AI agents effectively and quickly.
Merge
Merge Agent Handler uses Merge Link, an embeddable UI component, to help users authenticate with a given connector.
For example, say a user asks your AI agent to create a ticket in their project management system.
Merge Agent Handler can check if the user has the appropriate access to the project management system. If they don’t, Merge Agent Handler surfaces Merge Link; if they do, the agent goes on to perform the requested action.
Pros of authenticating with Merge Agent Handler:
- Comprehensive authentication and access controls: Our example above oversimplified the authentication process
Behind the scenes, Merge Agent Handler lets you organize connectors and tools into Tool Packs. You can then register users (representing individuals or service accounts) and link them to those Tool Packs using shared or individual authentication credentials, each with precisely defined access scopes.
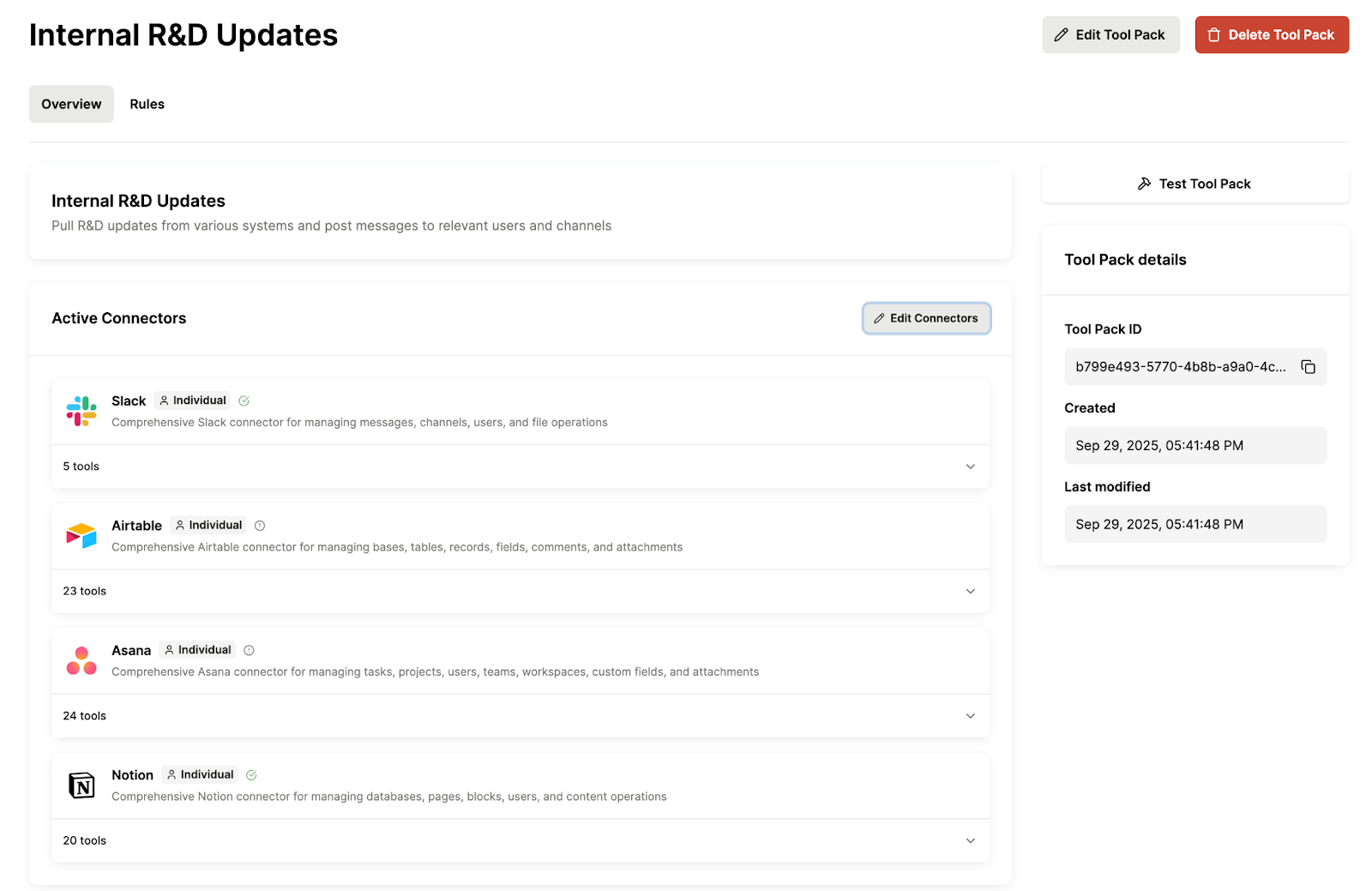
- Intuitive and seamless auth experience for users: The process of authenticating with Merge Link is incredibly simple for users, as Merge Link provides instructions and relevant links every step of the way. This leads to high success rates for authenticating and authorizing users and faster adoption of your AI agents
.png)
- Additional features and capabilities to keep data secure: Merge Agent Handler also lets you set rules on the data types your agents can and can’t share, track violations of these rules via alerts, use logs to diagnose and troubleshoot issues, and more
{{this-blog-only-cta}}
Composio
Composio takes a configuration-based approach to manage authentication for each connector.
Here’s how it generally works:
1. Creating and storing auth configs: Each connector has its own authentication “config.” You can define and store these configs in Composio to manage how users connect their accounts.
2. Authenticating the user: When a user connects to a toolkit (or a collection of pre-built tools), Composio handles the full OAuth flow and returns an auth config ID tied to that user’s credentials.
3. Running actions with the right credentials: To execute any action, you’d pass both the user ID and the auth config ID. Composio uses these to ensure the correct account and permissions are applied.
Pros of authenticating with Composio:
- Centralized and reusable auth management: You don’t have to build or maintain separate auth logic for GitHub, Slack, Notion, etc. Once a user authenticates, you get a reusable auth config id that works across your app and agents
- Managed credential storage & lifecycle: Composio handles the storage, refresh, and usage of access/refresh tokens on behalf of your app (when using its managed auth), so you don’t need to build your own token vault
- Simple API for multi-user and multi-connector scenarios: By passing both the user id and auth config id, you can easily handle multiple users using the same connector (e.g., multiple GitHub accounts) and one user connected to several connectors
Cons of authenticating with Composio:
- Manual, SDK-centric testing workflow: To validate a given auth flow, you’d need to use scripts; this excludes non-engineers from testing and makes it harder to scale auth tests
- Access variability post-authentication: Even if a user authenticates successfully, they may not be able to make certain tool calls based on their plan (i.e., "premium tool" usage is constrained on lower tier plans). This can lead to a confusing and frustrating user experience
- Limited authentication visibility post set-up: If and when authenticated toolkits are disconnected, Composio doesn’t provide the real-time alerts necessary to notify the relevant users and allow them to re-authenticate quickly
Related: The best alternatives to Composio
Arcade
Similar to Merge Agent Handler, when a user asks your AI agent to perform an action, Arcade verifies whether that user has granted the necessary permissions (scopes) to complete the request.
If the required scopes haven’t been authorized, Arcade automatically initiates an OAuth flow, prompting the user to authenticate and grant access; if authorized successfully, Arcade securely manages and reuses that authorization for future requests so the user doesn’t need to re-authenticate each time.
Pros of authenticating with Arcade:
- Support for multiple authentication methods: Arcade supports OAuth 2.0, API keys, and user tokens, ensuring that every potential tool can be authenticated
- Authentication during task-execution: By verifying the user's identity at the moment of authentication, Arcade ensures tokens are only granted to the legitimate user
- Strong leadership background in authentication: Their founding team has helped build authentication products (e.g., Stormpath); given their team’s expertise in securing applications and data, Arcade will likely continue to be a strong solution for authenticating AI agents
Related: Arcade.dev's top competitors
Cons of authenticating with Arcade:
- Access variability post-authentication: Like Composio, Arcade prices their tools differently (some are “basic tools” while others are “advanced tools”). This can lead to tool calls failing for users that aren’t on the right plan
- Limited track record: Arcade has only received seed funding, was founded in 2024, and has a limited customer base. As a result, their auth implementations may not be fully battle tested and scalable
- Insecure community MCP servers. Several of Arcade’s community MCP servers may skip proper authentication workflows, leading your agents to grant unauthorized access to sensitive data
{{this-blog-only-cta}}







.png)


